Free Cybersecurity Course
Enter the cybersecurity field with our free introductory course. Learn the basics and build a strong foundation.
As our sensitive information is increasingly digitized (if not entirely digital), cybercrime is likewise on the rise. For most organizations, their security operations center (SOC) analysts, fill the role of digital watchdogs as they monitor and audit a company’s existing system for breaches.
If you’re at all familiar with the field of cybersecurity, that job description may sound fitting for other roles too, and it’s a frequent point of confusion—how does an SOC analyst differ from, say, a cybersecurity analyst or a penetration tester?
That’s why we’ve compiled this guide. Below, we’ll detail what an SOC analyst is, what they do, and how to become one yourself.
What Is a Security Operations Center (SOC) Analyst?
An SOC analyst is a person who works on a team to monitor, analyze, and respond to security issues. The main goal of SOC analysts is to prevent attacks on a network. They monitor the network for signs of an attack. Once an attack has been detected, they investigate it with other team members.
What Does an SOC Analyst Do?
An SOC analyst is responsible for monitoring and auditing the company’s systems. They also monitor network activity and ensure that no suspicious activities are happening. The SOC Analyst also works with other departments of the company, such as human resources or sales, to ensure that their systems are secure. If someone in one of those departments has an issue with their work computer, it will be up to the SOC analyst to correct it.
Here are a few of the responsibilities SOC analysts have:
Surveillance of an Organization’s Networks and Systems
An SOC analyst’s role is to monitor an organization’s IT infrastructure. This includes monitoring security systems, applications, and networks for any irregularities that may indicate a breach or attack.
Identifies, Assesses, and Mitigates Security Threats in Real-Time
When the SOC analyst identifies a threat, they will work with their team to determine what caused the anomaly within the system and how they can prevent it from happening again.
Incident Response and Investigation
Suppose an incident needs further investigation or action taken by law enforcement agencies. In that case, the SOC analyst will work with other team members to investigate the incident further before reporting to law enforcement agencies if necessary.
After investigating each incident thoroughly, they will also report any new knowledge gained about existing cyber threats or vulnerabilities within their network so that future incidents can be prevented, if possible, through updates applied immediately.
Collaborates With Other Team Members To Implement Security Procedures, Solutions, and Best Practices
SOC analysts collaborate with other team members to ensure that the company has the correct procedures in place to continue to operate safely and securely. This includes implementing new systems as well as updating existing ones when necessary.
Stay Up-to-Date on the Latest Security Threats
SOC analysts must maintain up-to-date knowledge about the latest cyber threats to their organization’s security, whether educating themselves on new phishing attempts or keeping tabs on which malicious actors are currently using hacking tools. This knowledge allows them to act quickly on any potential issues before they become problems for your company.
Participates in Security Audits
Security audits are essential to maintaining your organization’s security, as they allow you to identify vulnerabilities before hackers or malicious actors can exploit them. An SOC Analyst participates directly in these audits by helping with preparation and reviewing data afterward.


Become a Cybersecurity Analyst. Land a Job or Your Money Back.
Conduct vulnerability assessments into on-premise and cloud security risks. Work 1:1 with an industry mentor. Graduate with a CompTIA Security+ Certification. Land a job — or your money back.
How Can You Become an SOC Analyst?
Becoming a SOC analyst is an exciting and challenging process involving learning and practicing the skills required to solve problems, gather information, and make decisions based on your data.
Here are some of the most important steps you can take to help you get into SOC and become an effective analyst:
General Requirements
Make sure you tick all these boxes before you start applying for SOC jobs:
Education
While it can be beneficial, pursuing a bachelor’s degree in computer science or some other STEM-related subject isn’t necessary to become an SOC analyst. Instead, many analysts get into cybersecurity after taking a cybersecurity course or enrolling in bootcamps. These will help you learn how to analyze data and spot patterns that may indicate a security breach is underway.
Certifications
There are a lot of certifications out there, but only a few can help you get cybersecurity jobs. Here’s a list to help you decide which one is right for you:
- CompTIA Security+
This is an excellent entry-level cybersecurity certification for anyone who wants to get into the security field. It covers security access control, cryptography, and risks in cloud computing. It’s also one of the best certifications for getting your foot in the door at many companies that specialize in cybersecurity.
- CompTIA CySA+
This certification focuses on network and application security and covers topics like secure configuration of firewalls and proxies, vulnerability assessment, and penetration testing. This is an excellent certification for anyone who wants to work in IT security or management.
- Certified SOC Analyst (CSA) by EC-Council
The CSA certification from EC-Council is an excellent choice for anyone who wants to specialize in incident response or threat hunting within their organization’s SOC. The CSA designation requires experience and demonstrated knowledge.
Related Experience
To start a career in SOC analysis, you’ll need to understand how the industry works. The best way to start is by working in SOC for a few years. This will give you an insider’s perspective on what it’s like to work as an analyst and help you develop your own toolset and build your skillset.
If you don’t have that kind of experience yet, then try freelancing or doing an internship.
Essential Skills

An SOC analyst needs several technical skills, such as intrusion detection and incident response. They also need soft skills, like critical thinking and problem-solving.
- Technical Skills
Let’s take a look at some of the different kinds of technical skills you’ll need as an SOC analyst:
- Intrusion detection: Detecting intrusions in your organization’s computer systems. This can include everything from malware infections to future security breaches in network security.
- Incident response: The ability to track down and mitigate an attack on your systems.
- Risk management: Understanding certain activities’ risks and making informed decisions about whether or not they’re worth it (or whether they can be made safer).
- Ethical hacking: The ability to hack into computer systems without breaking laws or regulations and use that knowledge for good instead of evil. This is also known as penetration testing or vulnerability scanning.
- Soft Skills
The world of cybersecurity is constantly evolving, and you need to keep up to stay competitive. But what kind of soft skills do you need? And how can you get them? Here’s a list of some of the most important ones:
- Problem-solving. This is essential for any role in IT. You must solve issues and problems with management and co-workers daily.
- Organizational skills. These are crucial for success in this field. You will be working with large amounts of data you must organize to make sense of it.
- Critical thinking. This is essential because everything you do as an SOC analyst involves critical thinking. You will have to think critically about every action you take in your role and how it affects the company.
How To Become an SOC Analyst

If you’re interested in becoming an SOC analyst, there are several steps you can take to get there.
Strong Fundamentals
This means being familiar with how computers work and how they interact with one another. It also means knowing about basic programming languages and computer networking.
Meet the Educational Requirements and Polish Your Skillset
In addition to the basics of computer science and networking, you’ll need a solid understanding of cryptography and data management techniques such as hashing and encryption.
Take On Volunteer or Freelance Projects To Build Your Portfolio
Volunteer or freelance for an organization that needs a lot of SOC analysts—like a big tech company or law enforcement agency. You can build up your experience while helping them solve their problems.
You could also offer your services on sites like Upwork or Fiverr, where clients post projects they need help with, and freelancers bid on them. It’s a great way to get real-world experience working with clients and solving their problems in the field, even if it’s only temporary work.
Pursue an Internship
An internship is a great way to get hands-on experience with SOC analysts’ security monitoring tools and processes and learn more about the field. Many companies offer internships for SOC analysts, so you should be able to find one that works with your schedule.
Find a Mentor
A mentor is a great way to ensure you’re on the right track and learn how to do things the right way. Mentors can help you get work experience, connect you with others in the field, and give feedback on your progress. If possible, find a mentor already working as an SOC analyst so they can tell you what it’s like.
Network
When it comes time to start looking for work, don’t forget about networking! Connect with other professionals through social media like LinkedIn or Reddit so that they’ll already know who you are and what kind of person they’re dealing with when job opportunities arise.
From the Experts: How Can You Succeed as a SOC Analyst?
An analyst should be able to work with a set of information security solutions that are used in a particular industry. It is not always necessary to know how exactly specific programs should be administered. However, it is always required to have a deep understanding of software and hardware capabilities, network architecture. It is also important to understand peculiarities of interaction between different solutions. It may be impossible to make conclusions basing on one cybersecurity event, however, it is possible if a few events are considered.
A good analyst’s background may vary – from a system administrator to CIO. But the person definitely needs to have strategic thinking and the ability to overview the whole situation.
Alex Drozd @ SearchInform
A career in SOC is largely a career in data analysis in my opinion. Knowledge of being able to manage, manipulate and triangulate large datasets is very useful for a career in SOC. Knowledge of tools such as splunk is extremely useful. In addition, being able to manipulate data with knowledge of code like python would be a huge advantage to staying relevant and growing in a SOC career
Abhay Bhargav @ AppSecEngineer
Rather than a narrow specialized skill, a great SOC analyst needs a diverse background and experience. On any given day their work might touch on engineering, architecture, or analysis across networks, applications, clouds, IoT, or really any specialty domain in a corporate environment. A SOC analyst’s primary role is to work with tools across the disciplines by taking logs, and compiling outputs to build, monitor, and triage potential security events in a business.
It may sound obvious, but a great place for a SOC analyst to start is working in IT. This could involve helpdesk, network engineering, or even application operations. Because these roles can involve tasks like building log outputs and reviewing system configurations, they can be a valuable training ground for future SOC analysts.
Nathan Cole @ Network Assured
Arguably one of the most important skills a SOC analyst needs is organization. When an incident occurs, it is paramount to start building a story to answer the following questions: what happened, is it still happening, and who is responsible? To be able to answer these questions, in the best and most efficient way, it is imperative to stay organized.”
Benjamin Wireman @ The Lifetime Value Co
Keep an online journal of interesting tickets that you managed. Record the history of the ticket, how you identified it, log sources and indicators of compromise. Also record how you interacted with your clients and how you helped them resolve their issues. You’ll review this journal periodically and add portions of this to your resume.
Aaron Cooper @ Nuspire
SOC Analyst Career Progression
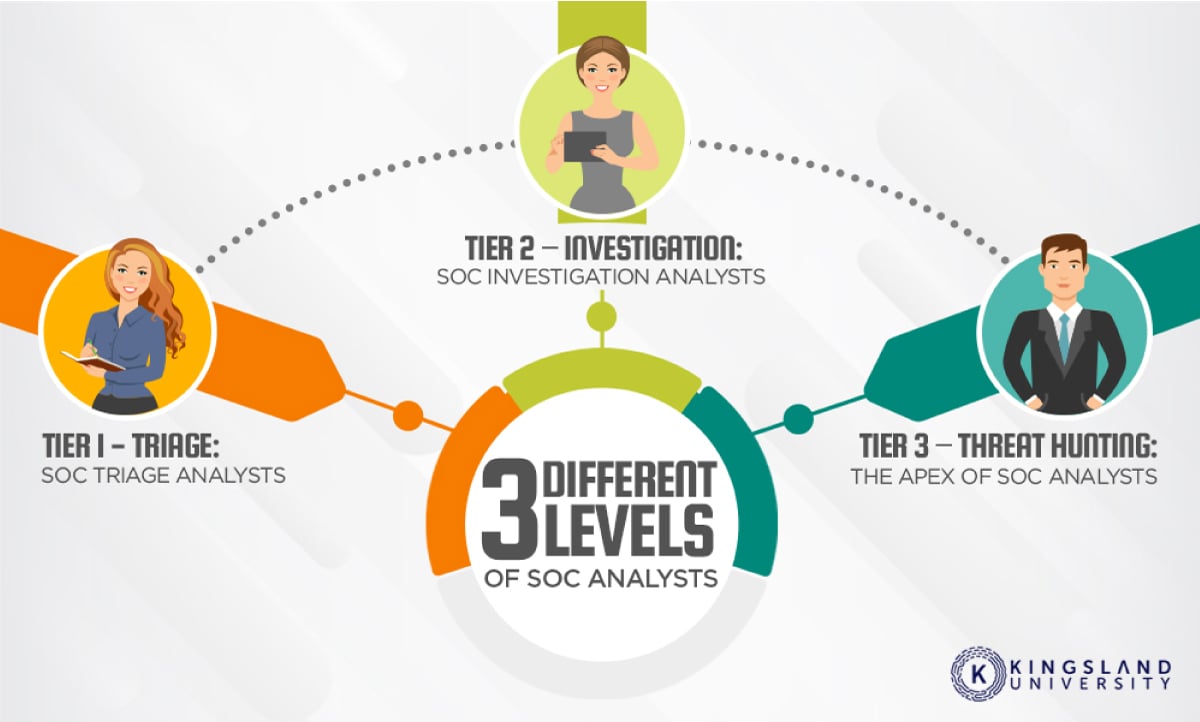
An SOC analyst’s career progression is an exciting and rewarding one, with plenty of growth opportunities and job titles. But to get there, you need to be prepared with the right skills and knowledge base. Here’s what that looks like:
Tier 1 SOC Analyst: Triage Specialist
A tier 1 SOC analyst is responsible for triaging incidents and making sure that they are handled appropriately. They will be tasked with deciding which incident needs further investigation and which can be closed or resolved quickly.
Tier 2 SOC Analyst: Incident Responders
A tier 2 SOC analyst is responsible for responding to an incident by performing investigation and mitigation activities. They will also work with other stakeholders (e.g., security engineers) to resolve issues with the system under attack.
Tier 3 SOC Analyst: Threat Hunters
A tier 3 SOC analyst is responsible for hunting down threats within an organization’s network or infrastructure. They will use their knowledge of threat intelligence information to find out where these threats may have originated from, whether they pose any real danger to the organization, and how they can be stopped before causing any damage.
SOC Engineer
An SOC engineer is responsible for designing, managing, and maintaining a security operations center (SOC). This person will work closely with other team members to ensure that everything works correctly both daily and when there are incidents occurring on their network/infrastructure.
SOC Manager
An SOC manager can have anywhere from 10 to 20 years of experience, depending on their previous roles within the company. They are responsible for managing the day-to-day operations of the SOC team and ensuring that they meet all requirements set by management.
Get To Know Other Cybersecurity Students
Dylan Wood
Cyber Threat Analyst at Trustwave Government Solutions
Rafael Ayala
Mergers And Acquisitions at Autodesk
Jose Mendoza
Cyber Security Career Track Student at Springboard
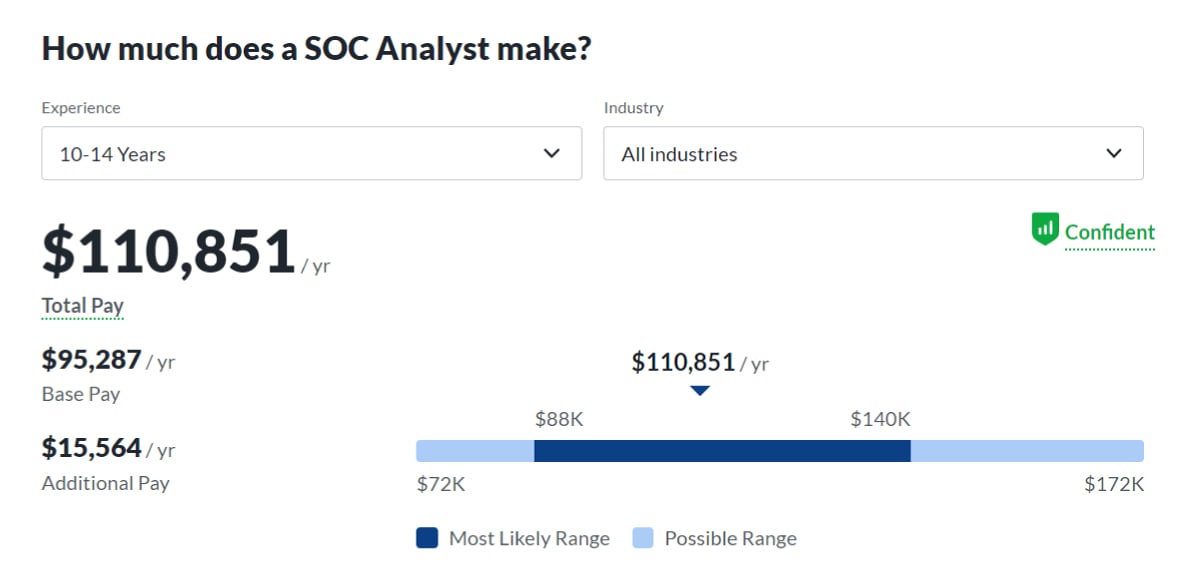
How Much Can You Earn as an SOC Analyst?
If you’re considering a career as an SOC analyst, you may be wondering how much money you can expect to make. Here are the salary ranges based on years of experience:
Entry-Level
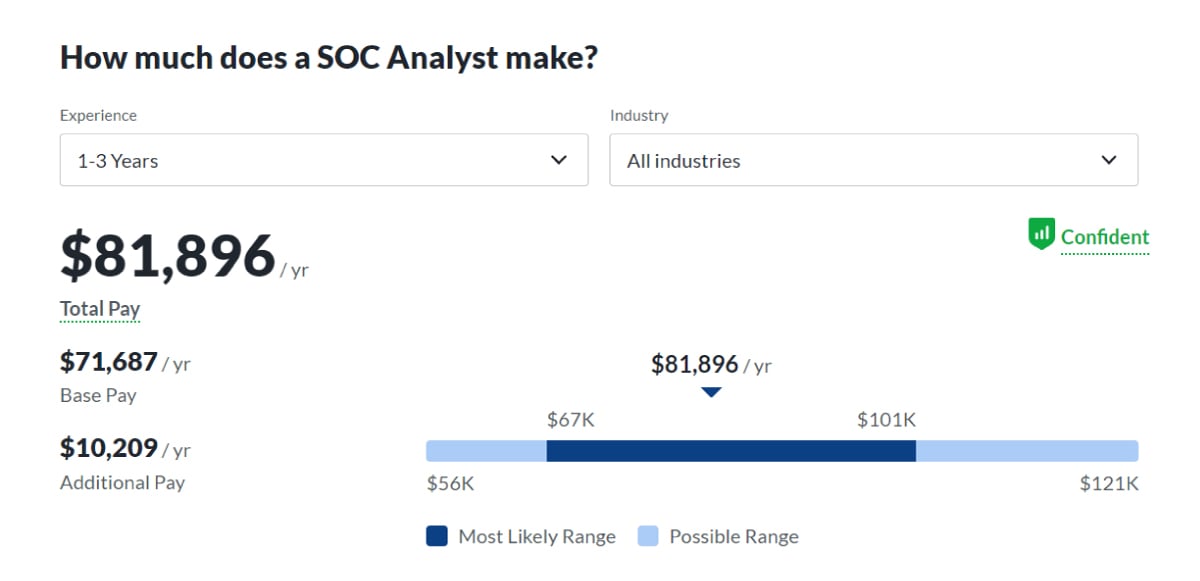
An entry-level SOC analyst with 1-3 years of experience can expect to earn an average salary of $81,787 per year.
Mid-Level
Mid-level SOC analysts earn an average of $90,537 annually.

Senior Level
Senior-level SOC analysts with 10-14 years of experience can earn up to $110,749 annually.
SOC Analyst FAQs
We’ve got answers to your most frequently asked questions:
What Is the Difference Between an SOC Analyst and a Cybersecurity Engineer?
The difference between an SOC analyst and a security analyst is that the former is responsible for monitoring, managing, and protecting systems against cyber attacks, while the latter focuses on identifying and stopping malicious activity.
An SOC analyst typically has a background in information technology (IT) or computer science. They monitor networks for unusual activity or vulnerabilities and may also be responsible for responding to security incidents by implementing countermeasures such as system patches or new firewalls.
Cybersecurity professionals typically have backgrounds in criminal justice or law enforcement. They use their investigative skills to identify malicious attacks on networks and operating systems as they happen so that they can be stopped before they cause harm.
Is Being an SOC Analyst a Hard Job?
Being an SOC analyst takes a lot of time, patience, and skill. The job requires you to be constantly on your toes and ready for anything. You will have to deal with hundreds of incident alerts and false positives daily, which can be very stressful.
SOC analysts are required to have strong knowledge about malware, hacking techniques, and other related topics. This is because they need to understand how hackers operate to properly detect and prevent them from causing harm.
Do You Need To Know Coding To Be an SOC Analyst?
If you want to be an SOC analyst, you should know how to code. Specifically, learning Golang, JavaScript, Python, or C++ will be helpful to those who want to work as an SOC analyst. These languages are some of the most commonly used by SOC analysts today, and learning them will help you get ahead in this field.
Since you’re here…
Interested in a career in cybersecurity? With or Cybersecurity Bootcamp, you’ll get a job in the industry, or we’ll return your tuition money. Test your skills with our free cybersecurity course, and check out our student reviews. We’re a safe bet. 🔒😉






