Free Cybersecurity Course
Enter the cybersecurity field with our free introductory course. Learn the basics and build a strong foundation.
As consumers become increasingly aware of the importance of data privacy, the demand for information security analysts—professionals tasked with protecting an organization’s data—is growing exponentially. According to the U.S. Bureau of Labor Statistics, information security analyst roles are projected to grow 33% from 2020-2030, much faster than the average growth rate for other occupations.
If this lucrative and growing career sounds appealing to you, then you may be wondering: how do I become an information security analyst? With this guide, of course! Below, we’ll detail what an information security analyst does, what technical and soft skills you need to become one, and where to find your first job.
What Is an Information Security Analyst?
Information security analysts protect organizations from data breaches and hacks. They develop, implement, and enforce security standards to protect sensitive information by performing risk assessments, installing and implementing security controls, and doing cyber defense planning to prevent future security incidents.
What Does an Information Security Analyst Do?
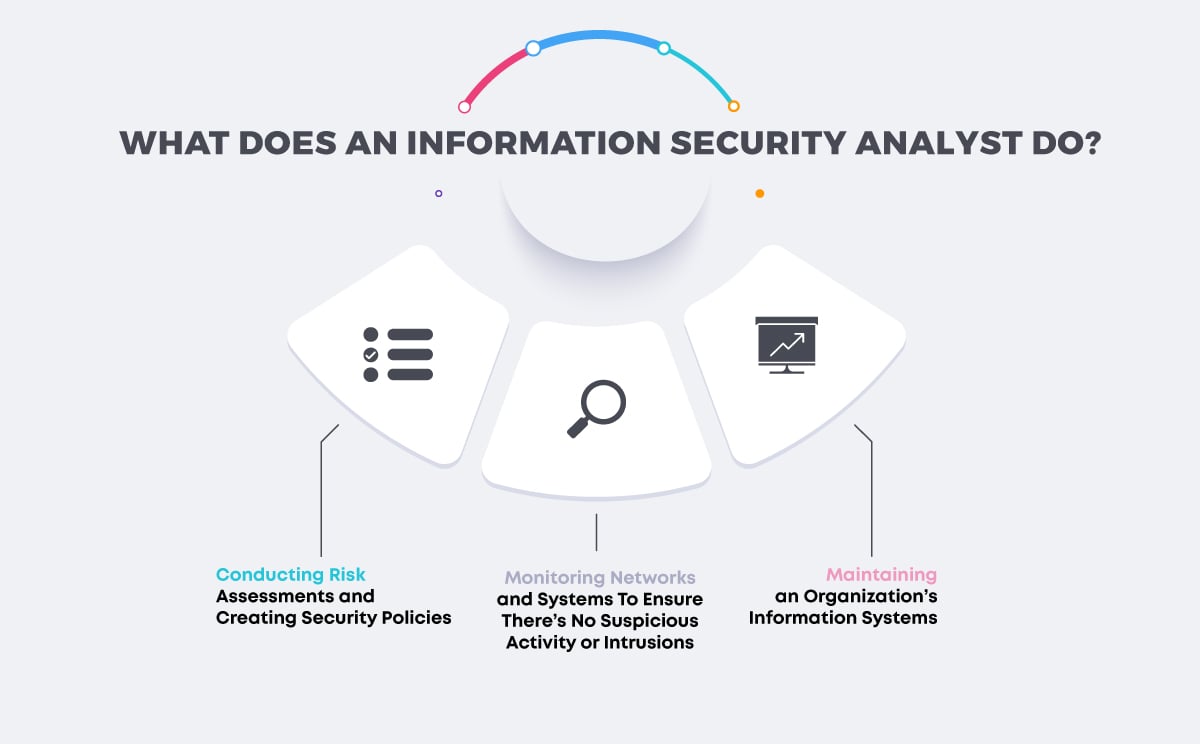
Security analysts have a range of responsibilities, from designing and implementing security controls to incident response and educating employees about security best practices. Here’s what that looks like in practice:
Maintaining an Organization’s Information Systems
Information security analysts protect the data and information of an organization, its employees, and customers. Examples include personally identifiable information (PII) and intellectual property. Analysts are responsible for monitoring and maintaining network security, application security, and physical security.
Monitoring Networks and Systems To Ensure There’s No Suspicious Activity or Intrusions
Analysts use and maintain firewalls and data encryption programs to protect sensitive information. They may also deploy defensive AI software to check for vulnerabilities in computer and network systems and to perform automated incident responses in the event of a breach.
Conducting Risk Assessments and Creating Security Policies
Information security analysts assess an organization’s ability to protect its information systems from breaches and devise security measures to correct errors. They also study industry trends to forecast future attacks based on the current threat landscape.
Responding to Security Incidents, Investigate, and Provide Support
A security specialist performs incident response in the event of an attack. They investigate the nature and severity of the threat, determine if the intruder is still in the system, perform a root cause analysis, and take preventative measures to avoid a recurring attack.


Become a Cybersecurity Analyst. Land a Job or Your Money Back.
Conduct vulnerability assessments into on-premise and cloud security risks. Work 1:1 with an industry mentor. Graduate with a CompTIA Security+ Certification. Land a job — or your money back.
How To Become an Information Security Analyst
-
Pursue a Computer Science Degree (Not Mandatory)
-
Learn the Fundamentals
-
Understand the Tools
-
Complete a Course or Bootcamp
-
Find a Mentor
-
Pursue an Internship
-
Consider Getting Certified
-
Develop a Strong Portfolio and Tailor Your Resume to Each Job You’re Applying For
Information security analysts must be familiar with cybersecurity fundamentals, how to configure, install, and monitor cybersecurity controls, and communicate with stakeholders. Here’s how they can go about learning that:
Pursue a Computer Science Degree (Not Mandatory)
While a degree in cybersecurity or a computer-related field is helpful, it’s not the only way into the career field. Some employers prefer to hire analysts who have professional certifications such as the CompTIA Security+ (available through Springboard’s Cybersecurity Career Track), CySA+, CISA, or CISSP.
Learn the Fundamentals
These cybersecurity fundamentals provide the cornerstone for any successful cyber strategy:
CIA Triad

Source: Varonis
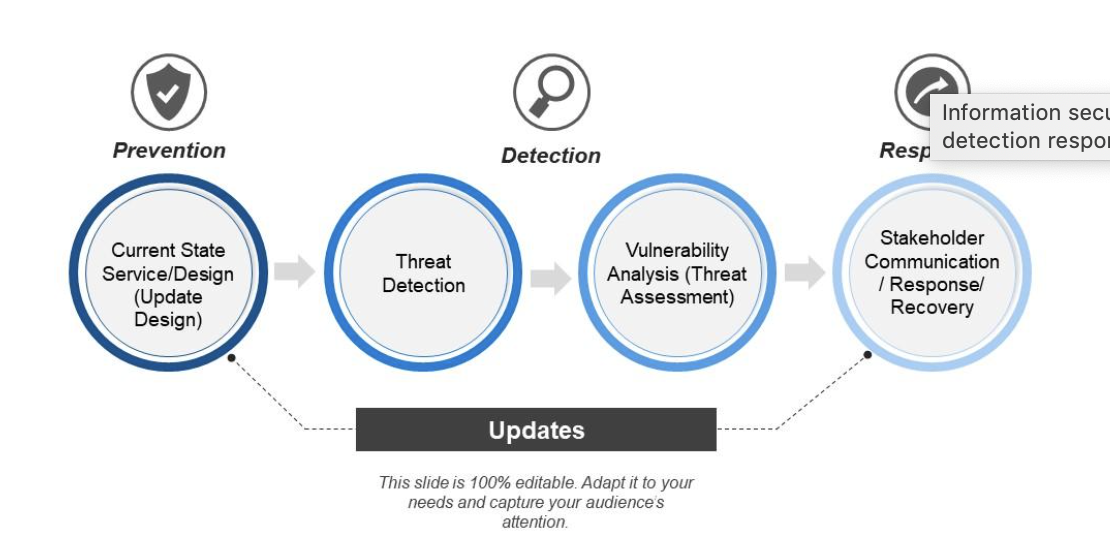
Information Security Process (Prevention, Detection, Response)
The CIA triad (which stands for confidentiality, integrity, and availability) is a common model that explains the main objectives of any cybersecurity framework. This model helps security teams ensure all bases are covered using security best practices.
The information security process consists of many strategies, but we can group them into three distinct categories—prevention, detection, and response.
Preventing cyberattacks is a multi-step process that includes erecting firewalls, encrypting files stored in the cloud, configuring access controls, conducting security awareness training programs, and installing and configuring antivirus software to prevent malware from infiltrating computer systems. Firewalls (a network security device that monitors traffic to and from a computer network) are typically an organization’s first line of cyber defense.
Organizations must also have a defensive strategy in the event of a cyberattack or security violation. First, they must detect intruders in a timely manner using an intrusion detection system (IDS), which performs 24/7 networking monitoring. These systems detect attack signatures and generate alerts when suspicious activity is detected.
Finally, organizations must create an incident response plan in advance. In the event of an attack, security professionals follow procedures outlined in the organization’s Cyber Security Incident Response Plan (CSIRP). They must work with the incident response team to declare the incident, coordinate activities of the response team, and communicate status reports to upper management. Ultimately, their job is to expel the intruder, determine how much damage is done, and restore compromised systems using a disaster recovery plan.
Get To Know Other Cybersecurity Students
Karen Peterson
Compliance Advisory Associate at Coalfire
Ed Burke
Cyber Security Career Track Student at Springboard
Catherine McKoy
Consumer Compliance Systems Analyst at Alaska USA Credit Union
Understand the Tools
Information security analysts must use a range of tools and techniques to protect organizations from outside attacks and internal weaknesses.
Intrusion Detection and Prevention
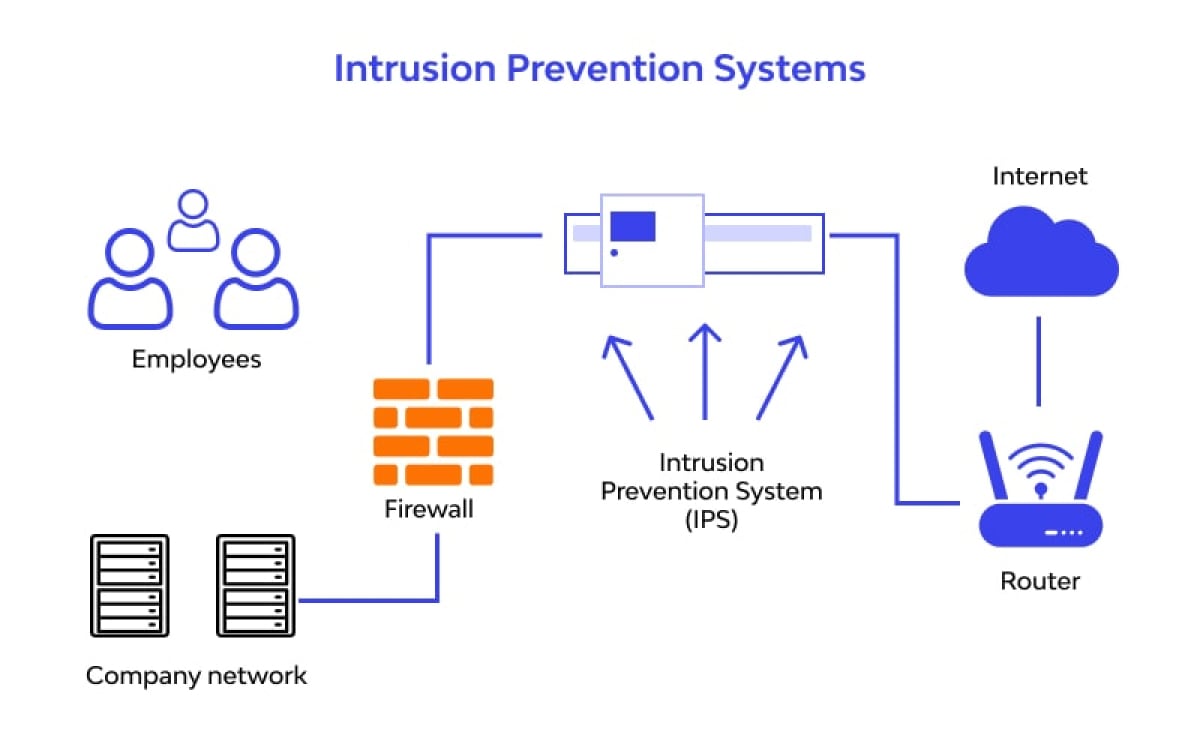
Intrusion Detection and Prevention Systems (IDPS) monitor network and IT environment activity to detect malicious activity in real-time and block intruders either through an automated response or by alerting a security professional.
Firewall
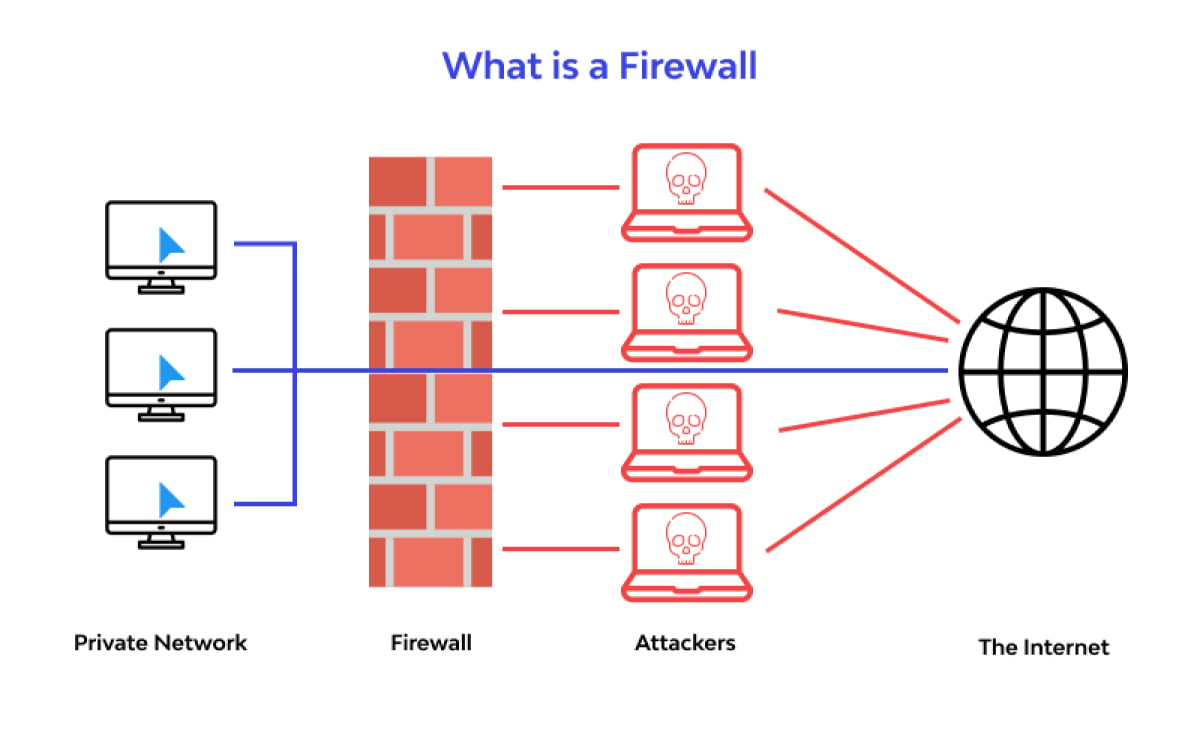
A firewall is a network security device that monitors incoming and outgoing traffic within a network. It allows or blocks traffic based on a defined set of security rules. Firewalls also create a barrier between a private internal network and the world wide web.
Encryption
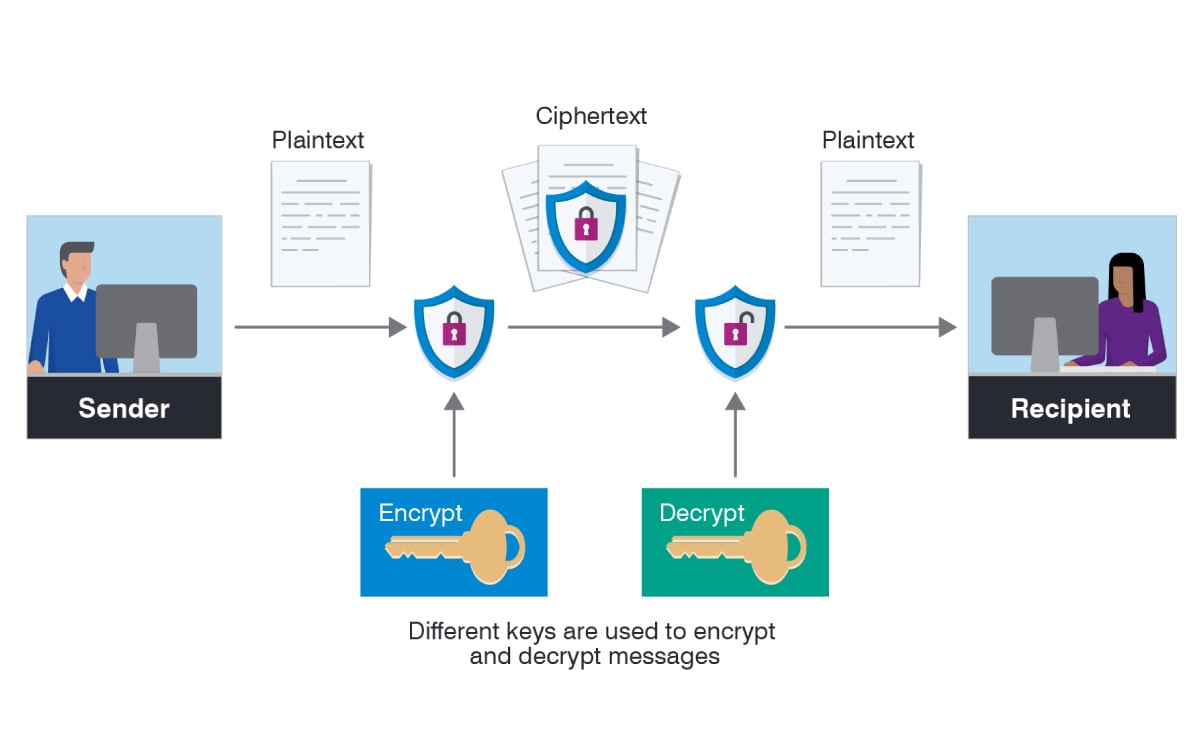
Encryption is a way of scrambling data to make it unreadable (converting it from plaintext to ciphertext). Ideally, only authorized users have the decryption key needed to decipher a ciphertext back to plaintext and access the original information.
Security Incident and Event Management (SIEM)
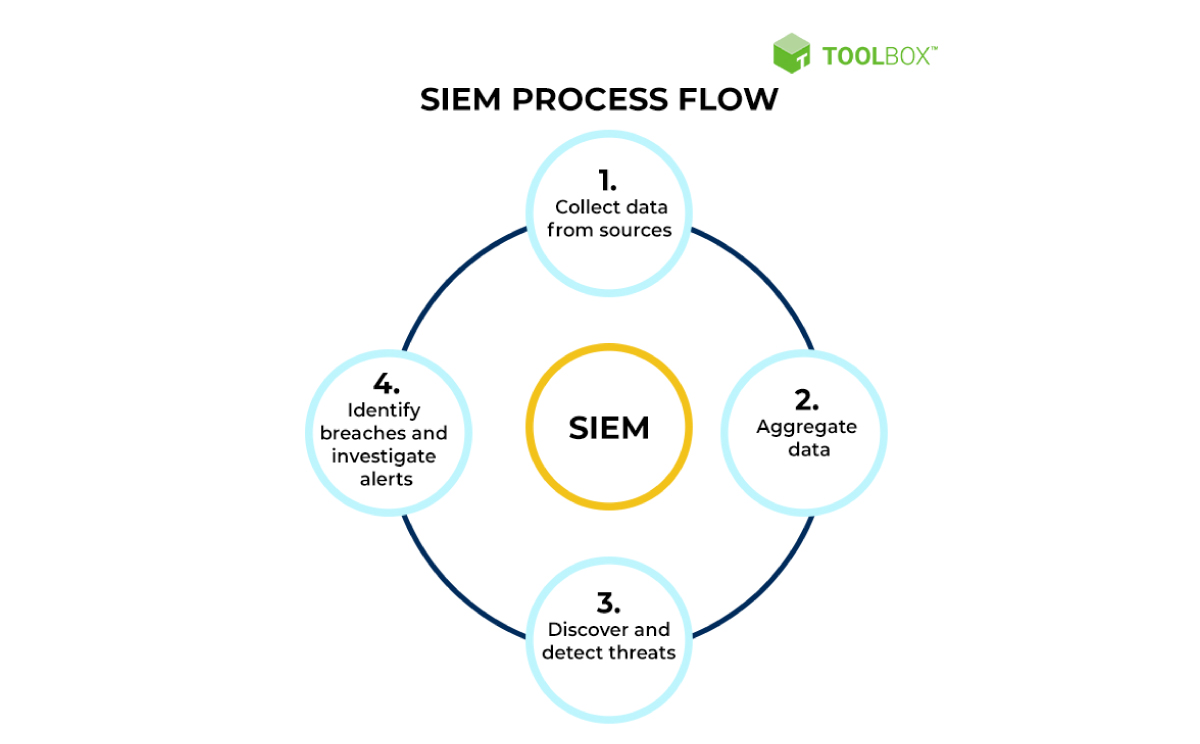
Source: Spiceworks
SIEM is real-time monitoring and analysis of security events. The system also logs security data for compliance or auditing purposes. SIEM combines SIM (security information management) and SEM (Security event management) functions into one security management system. The system collects and analyzes cyber threat intelligence and performs incident management.
Data Loss Prevention

DLP software detects and prevents potential security breaches that could result in data loss or data leakage. Organizations use DLP to protect their data and comply with regulations. It is meant to protect personally identifiable information (PII) or intellectual property. Aside from detecting intruders, a DLP enables a network administrator to control what information employees can share outside of the corporate network.
Access Control
Access control is a process by which organizations determine user permissions to grant or revoke access to corporate data and resources. It also includes procedures for authenticating users (identity verification) and ensuring appropriate access status is granted to users.
Endpoint Security
Endpoint security is the process of securing end-user devices such as computers, laptops, and mobile devices from being exploited by malicious actors. These security measures have become increasingly important as remote employees use home Wifi networks and privately owned devices, which are typically less secure than corporate networks.
Complete a Course or Bootcamp
Bootcamps and online courses prepare you for entry-level roles in cybersecurity. Your best option is to find additional training that provides you with a certification and a portfolio of work that enables prospective employers to validate your skills. Springboard’s Cybersecurity Career Track offers a 100% online 6-month program that enables you to build job-ready skills. You’ll complete 30 labs, 35 mini-projects, and a capstone project based on real-world scenarios showcasing your skills to hiring managers, while working 1:1 with an expert mentor. At the end of the program, you’ll prepare to sit for the CompTIA Security+ certification exam.
Find a Mentor
Receiving mentorship from an industry expert will help you understand the real-world applications of the tools and concepts you’re learning, while also providing you with an insider’s perspective on job-hunting, negotiating, and working in the field.
Pursue an Internship
Internships provide hands-on experience in a real production environment and enable you to solve problems for a real client. This work experience might result in projects you can display in a portfolio as well as case studies to bring up during interviews to give hiring managers insight into your problem-solving skills.
Consider Getting Certified
Industry-recognized certifications help prospective employers validate your skills and job readiness. Some certifications are domain- or vendor-specific while others prepare you for generalized jobs in cybersecurity. Here are some of the most common certifications:
CompTIA Network+

This certification validates the technical skills needed to securely establish, maintain and troubleshoot the essential networks that businesses rely on. The CompTIA Network+ certification is best for those aspiring toward a network security or network administration role. You’ll learn networking fundamentals, network implementation, security, operations, and troubleshooting.
CompTIA Security+

This certification validates the baseline skills necessary to perform core security functions and pursue an IT security career. According to CompTIA, this certification is chosen by more corporations and defense organizations than any other certification on the market to validate baseline security skills. It covers the core technical skills in risk management, incident response, forensics, and hybrid-cloud operations.
GIAC Information Security Fundamentals (GISF)

This entry-level certification validates your knowledge of cybersecurity fundamentals. It shows you understand key security concepts including networking, introductory cryptography, and cybersecurity technologies.
Develop a Strong Portfolio and Tailor Your Resume to Each Job You’re Applying For
A cybersecurity portfolio should demonstrate your knowledge of cybersecurity fundamentals, show practical experience with important techniques, and outline your thought process when designing cybersecurity solutions. Include cybersecurity projects that demonstrate a range of skills like threat detection and mitigation, identity access and management (IAM) governance, and remediation tactics. An ideal project builds upon your current strengths while presenting challenges to build your skills. Tailor your resume to each position by frontloading the most relevant experience and changing your summary, if you choose to include one.
Information Security Analyst Skills
Entry-level security analysts need a range of technical and soft skills to succeed on the job.
Technical Skills
Here are the technical skills you’ll need to succeed as an information security analyst:
Knowledge of Cybersecurity Fundamentals
You must know the basics of developing a security platform, as well as how to set up and configure security systems. More specifically, you must know how to detect threats, protect systems and networks, and anticipate potential cyberattacks.
Risk Analysis and Management
You must be able to determine the critical assets in an organization’s IT infrastructure, create a risk profile for each one depending on the type of data the asset creates, stores, or transmits. Next, you must define a mitigation approach and enforce security controls to guard against known risks.
Network Security
You must know how to protect computer networks using both software and hardware technologies. In this role, you’ll be responsible for configuring, installing, and implementing secure network systems. You’ll also need an understanding of wired and wireless networks and how to secure them.
Security Architecture
Security architecture consists of the tools, processes, and technologies used to protect a business from external threats. You must understand the relationships and dependencies of these various components and how they work to mitigate threats, strengthen security protocols, and manage security controls to protect enterprise infrastructure and applications.
Data Protection Principles
Data protection principles are the seven core principles identified by the GDPR for the lawful handling of personal data. This includes:
- Lawfulness, fairness, and transparency
Organizations must be transparent about how they use consumer data and should take care to process data lawfully. - Purpose limitation
Data should be limited to specified and legitimate purposes. - Data minimization
Organizations should only retain the smallest amount of data needed for their purposes. - Accuracy
Personal data must be accurate and kept up to date. - Storage limitations
Organizations must not store data longer than necessary and unused data should be deleted. - Integrity and confidentiality
Data should be protected from unauthorized access or accidental loss or damage. - Accountability
Organizations must demonstrate compliance with data protection principles.
Incident Response
You must know the steps used to prepare for, detect, contain, and recover from a data breach. To do this, you’ll need a conceptual understanding of how to implement an incident response plan, detect the threat and analyze its type and severity, contain and eradicate the threat, and initiate post-incident recovery.
Soft Skills
Security professionals shoulder a lot of responsibility. Having this combination of soft skills will help you excel in your career and deliver better results:
Problem-Solving
Information security analysts must think of innovative ways to address security issues and identify threats. They must be able to study computer systems, identify security risks, and consider possible solutions. Problem-solving is key because you must always think one step ahead of a cyberattack.
Communication
Writing skills are essential because information security analysts must document their work for compliance and auditing purposes. Technical writing skills are needed to write security guidelines and generate reports on security incidents. You must also be adept at active listening and communicating complex concepts to a non-technical audience as you may need to lead security awareness training.
Organization
With so many demands on their time, information security analysts must have good organizational skills. They must also know how to triage security alerts and determine which ones warrant intervention. They may also have to manage people or projects as they gain responsibility in their career.
Critical Thinking
A cyber intelligence specialist makes high-stakes decisions on a daily basis. Critical thinking skills entail asking the right questions, assessing data objectively, considering alternatives, and drawing data-driven conclusions.
Analytical Mindset
Analysts must be able to analyze and set up security tools and software and use cyber intelligence to determine the nature and severity of a threat. You’ll also need analytical thinking to evaluate competing security solutions and select the best one, and prioritize tasks in order of importance in the aftermath of a cyberattack.
Independence
Cyber network security analysts must be able to make decisions autonomously and take initiative in responding to security threats and making recommendations to strengthen an organization’s security operations.
Flexibility
You must be able to work in a fast-paced environment and perform well under pressure.
How Much Can You Make as an Information Security Analyst?
Information security analysts have numerous opportunities for promotion and are rewarded for pursuing further education or gaining years of experience. Here’s how that all breaks down:
Entry-Level Information Security Analyst
According to Indeed, entry-level information security analysts earn an average salary of $92,802/year.
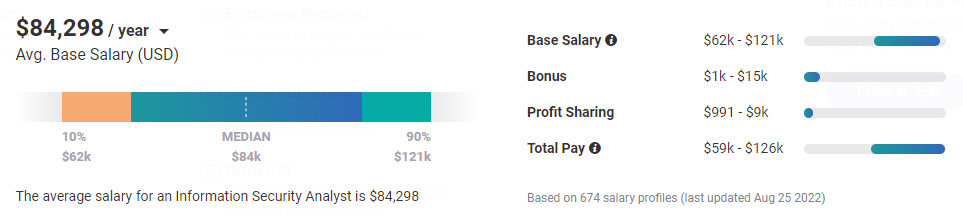
Mid-Level Information Security Analyst
According to Payscale.com, mid-level information security analysts earn an average salary of $84,298/year.
Senior Information Security Analyst
According to Payscale.com, senior information security analysts earn an average salary of $106,803/year.
Resources To Find Entry-Level Cybersecurity Jobs
Ready to launch your cybersecurity career? Start by looking for jobs in the following places:
Job Boards
Job boards are a great place to start if you don’t already have industry contacts. General-purpose job boards help you find a range of roles in security, while niche job boards make it easy to drill down job postings with specific titles or required skills.
General (Glassdoor, Indeed)
General job boards such as Glassdoor, Indeed, and LinkedIn display a range of security analyst positions. You can filter jobs according to industry, location, salary requirements, flexible work arrangements, and more.
Niche (Infosec-jobs.com)
To minimize competition and avoid having to filter out unsuitable jobs, try job boards that focus on cybersecurity roles. Examples include infosec-jobs.com, Careers in Cyber, and the Dice Cybersecurity Job Board.
Network (LinkedIn, Online Communities)
Your network is your biggest asset in finding your first security role. Find professionals on LinkedIn and request an informational interview, or join a cybersecurity forum for IT professionals, such as Malware Tips and Antionline (great for learning about industry trends), or TechExams Community (best for exam prep).
Information Security Analyst FAQs
We’ve got the answers to your most frequently asked questions.
Is Becoming an Information Security Analyst a Good Career?
Yes! Information security analysts perform critical work and are well-compensated.
The role ranks #25 in US News & World Report’s ‘Jobs That Pay 100K or More,’ which rates occupations according to median salary, job prospects, and current employment rate.
Is Coding Necessary To Be an Information Security Analyst?
Information security analysts do not need to code since much of their work involves analyzing machine data, configuring security controls, and responding to alerts.
However, programming ability helps you automate certain tasks and become more efficient
Can I Become an Information Security Analyst Without a Degree?
Yes. Most employers are willing to hire cybersecurity professionals with industry-recognized cybersecurity certifications. Advanced degrees may be necessary for higher-level positions.
What’s the Difference Between a Cybersecurity Analyst and an Information Security Analyst?
A cybersecurity analyst secures computer systems, networks, and applications from cyberattacks of any kind, such as malware attacks or SQL injection attacks. Information security analysts focus on protecting an organization’s data and information in both digital and physical environments.
This may include ensuring former employees don’t leak trade secrets or protecting intellectual property.
Since you’re here…
Breaking into cybersecurity doesn’t take a Trojan Horse. Our Cybersecurity Bootcamp lasts just six months, and we’re ready to help you land a job after graduation or your money back. There’s urgent need in this field, so we’re beaming out tons of freebies to entice you, like this email course on certifications and our guide to becoming a software security analyst. Join in—there are plenty of jobs to go around!







