Free Cybersecurity Course
Enter the cybersecurity field with our free introductory course. Learn the basics and build a strong foundation.
Hackers hit hard in 2014, releasing almost one million new strands of malware each day. While we’ve reached new encryption milestones since then—now more sites are HTTPS-secure, for example—malicious cyberattackers refuse to back down. A Symantec report revealed new mobile malware types last year increased by 54 percent. This is concerning, considering that malware ranked as the costliest cyberattack worldwide in 2017; according to an Accenture and Ponemon report, corporate malware victims across the globe lost $2.4 million per incident. Danish shipping powerhouse A.P. Moller-Maersk lost more: Last summer, Maersk (temporarily) buckled from malware juggernaut NotPetya, resulting in a loss of between $200 million and $300 million. (It took two weeks to get operations running as usual; in the meantime, Maersk employees were forced to get goods out using Twitter and WhatsApp—even Post-Its.)

(Image source: Accenture and Ponemon Institute)
Luckily, Moller-Maersk brings in billions: Maersk’s 2018 Q1 revenue growth of $9.3 billion makes the $200-$300-million-dollar cyber attack look like chump change. And that’s the point: most businesses don’t have that kind of revenue; most would fall and not get back up if sucker-punched by a multi-million-dollar cyber hit.
Implementing public-key infrastructure (PKI) is critical for small and medium-sized businesses (and large corporations) looking to fight back. Market forecasters already know this, with Market Research Future predicting the global PKI market will reach a staggering $1.99 billion by 2023, with a compound annual growth rate of over 22.7 percent between 2017 and 2023. Stay ahead of the curve and learn the PKI basics: What is PKI and what makes it a strong cybersecurity go-to? How does it work with other security practices to bolster cyber defenses? And why is it a great tool for those considering a career in cybersecurity?
Read More: What Does a Cybersecurity Analyst Do?
Get To Know Other Cybersecurity Students
Ed Burke
Cyber Security Career Track Student at Springboard
Dipen Patel
Cybersecurity Analyst at Accenture
Dylan Wood
Cyber Threat Analyst at Trustwave Government Solutions
PKI Basics: What Is Public-Key Infrastructure?
PKI is a framework that uses public-key encryption, along with policies, standards, and other hardware and software, to ensure there’s trust for all parties using data encryption. Specifically, a certificate authority is in charge of distributing digital certificates that verify the public-key owner and public key. If all checks out, the digital certificate is issued. Anyone involved in the data-encryption process can look up the sender’s or receiver’s public key to make sure it’s a match.
PKI in Action

Let’s revisit the hypothetical email example from the post on cryptography basics. Your boss needs specific company-sensitive information as soon as possible. Since it’s email communication, public-key encryption is the more secure of the two types (private-key encryption is used more for storage purposes). Your boss sends their public key to you; you send your public key to them. Now that both public keys are exchanged, the problem’s solved, right? Not quite.
Although both private keys remain secret, the public keys are not, which is the double-edged sword of public-key encryption: without proper certification identifying and authenticating your boss’ public key, you risk receiving—and using—an implanted public key. For all you know, that company-sensitive information could go to the wrong inbox, causing corporate mayhem and a potentially successful breach. This is why PKI is important. It supports and authenticates via digital certificate that your boss’ and your public keys belong to you. Negligent insider or malicious outsider attack averted.
PKI Matters: Why Implementing Public-Key Infrastructure Is a Must
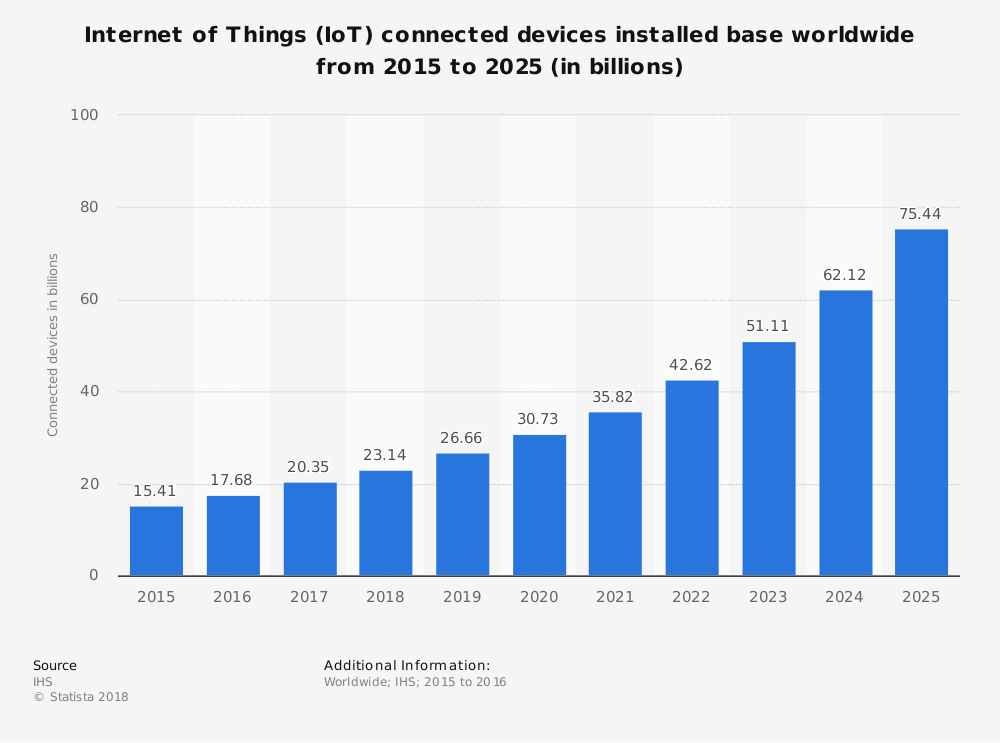
Source: IHS
A staggering 600 percent increase in IoT attacks in 2017 (50,000 in 2017 compared to just 7,000 in 2016) is unsurprising. The number of internet-connected devices shot up 2.79 points from last year, and it’s only going to continue hitting record highs: 35.82 billion in 2021, 51.11 billion by 2023, and a monstrous 75.44 billion in 2025. (IoT is even used for trash cans!) While IoT increases efficiency and scalability, it also increases cyber threats (and puts certain industries at risk for job extinction, but that’s a topic for another day).
Ninety-seven percent of risk professionals admit that a data breach taking advantage of unsecured internet-connected devices would be “catastrophic.” The large number of IoT devices and an effective process that authenticates all is a two-fold cyber challenge—one PKI can solve. Digital certificates on all IoT devices reduce the likelihood of a successful IoT-driven attack and, with more resources, help businesses trying to take inventory of IoT devices—only 15 percent of risk professionals claim to do this now.
Implementing PKI

(Image source: Verizon 2018 Data Breach Investigations Report)
The stats don’t lie: implanted malware is up by a whopping 200 percent, and nearly 40 percent of malware cases in 2018 so far are ransomware. The hacker’s motives? According to Verizon’s 2018 Data Breach Investigations Report, it can be sadistic: while most hackers launch full-fledged cyberattacks for financial gain, 11 percent wreak havoc on organizations for fun.
As if sadism wasn’t enough, new and improved hijacking software makes fighting cybercrime challenging. But thanks to PKI technologies and other cyber-defense strategies, it is not impossible. Implementing PKI strengthens your defenses and reduces the chance of a costly cyberattack. It’s fast to set up, keeps information confidential, and has long-term financial benefits (especially for industries like healthcare that must comply with strict HIPAA standards and protocols). Even governments are all for adopting PKI as an everyday defense strategy: Estonia replaced social security numbers—an identifier more exposed than ever to cyber threats, yet commonly collected in the U.S. by schools, banks, and companies—with citizen-issued smartcards linked to PKI.
With an emerging PKI market breaking out of its shell (projected to be a multi-billion-dollar industry in 2023) and a high demand for cybersecurity jobs, now is the time to get your PKI training started.
Since you’re here…
Interested in a career in cybersecurity? With or Cybersecurity Bootcamp, you’ll get a job in the industry, or we’ll return your tuition money. Test your skills with our free cybersecurity course, and check out our student reviews. We’re a safe bet. 🔒😉






