Free Cybersecurity Course
Enter the cybersecurity field with our free introductory course. Learn the basics and build a strong foundation.
Cybersecurity professionals play a critical role in safeguarding the digital universe, keeping information confidential and systems intact and protecting them from cyber threats posed by malicious actors. Whether it be ransomware attacks or data breaches, organizations around the world are in desperate need of cybersecurity specialists. There’s such a high demand for cybersecurity professionals that there will be an estimated 3.5 million unfilled jobs worldwide by 2025, according to Cybercert.
So if you’re interested in filling one of those 3.5 million positions, you should know the landscape of various career paths in the cybersecurity field. Navigating so many possibilities can be daunting, and you might find yourself in a dilemma about which direction to take. In this guide, we’ll demystify the various cybersecurity career paths and their prerequisites so you can decide which path to take.
The table below offers a brief overview of the top five career options. Or, skip to the details below:
What Does a Career in Cybersecurity Look Like?
Cybersecurity offers a dynamic and exciting career path in our increasingly interconnected world. A career in cybersecurity requires a blend of technical, analytical, and problem-solving skills. Cybersecurity jobs are more diverse than ever due to the exponential rise of technology, and range from ethical hackers to security architects, incident responders, cybersecurity analysts, and compliance auditors. This diversity ofroles makes the career path incredibly rewarding and challenging.
Remember that cybersecurity is a dynamic field, and the specifics of what a career entails can evolve as technology and threats change.


Become a Cybersecurity Analyst. Land a Job or Your Money Back.
Conduct vulnerability assessments into on-premise and cloud security risks. Work 1:1 with an industry mentor. Graduate with a CompTIA Security+ Certification. Land a job — or your money back.
What Are Some Different Cybersecurity Career Paths?
One of the most thrilling aspects of cybersecurity is thediverse array of available career paths, all tailored to different skill sets and interests. These range from highly technical roles like ethical hackers and security engineers, who work on the frontlines of cyber defense, to strategic roles like cybersecurity analysts and consultants, who evaluate security measures and guide policy.
Let’s dive deeper into some of these cybersecurity roles!
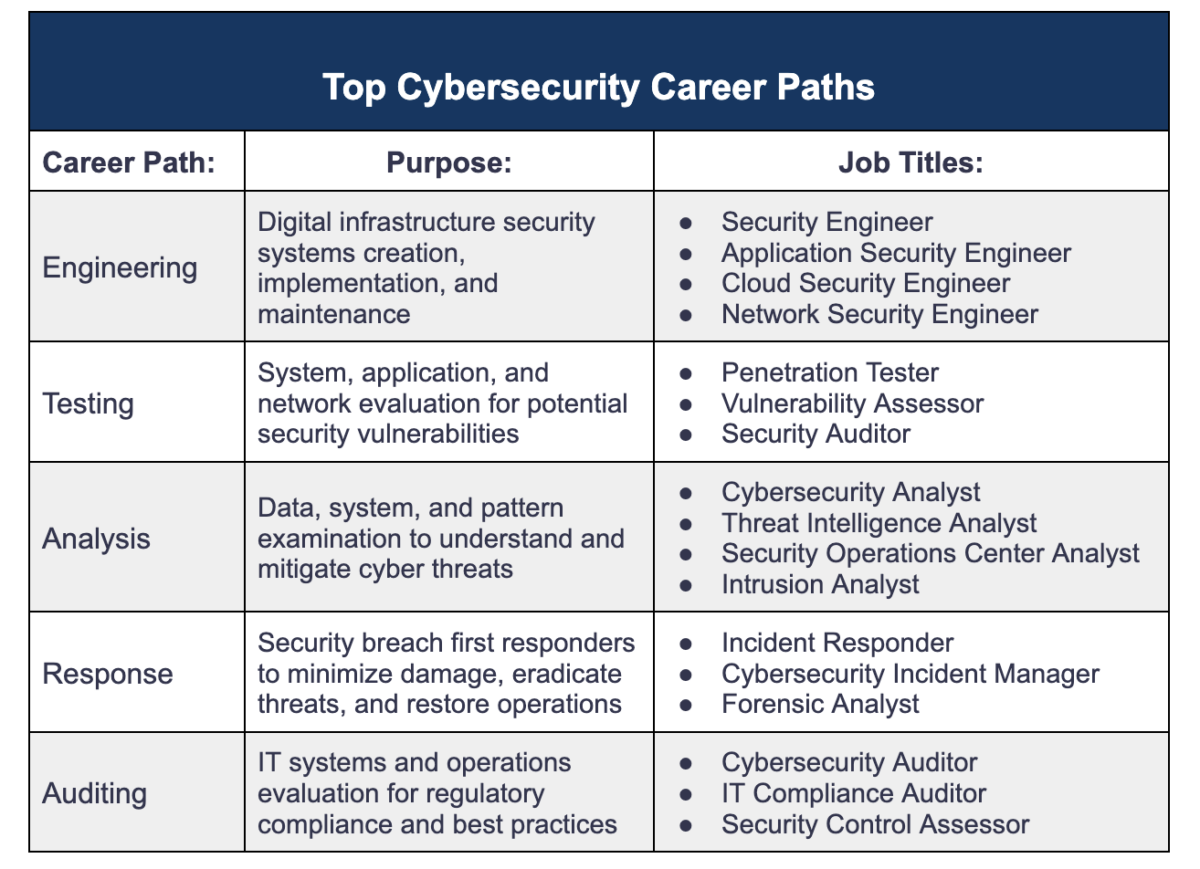
Engineering
In cybersecurity, engineering is the technical bedrock upon which all security measures and protocols are built.
Cybersecurity engineers are integral to creating, implementing, and maintaining the systems designed to protect an organization’s digital infrastructure. They use their knowledge of system vulnerabilities, software vulnerabilities, and network security to build strong defenses against cyber threats.
Besides developing and implementing security systems, these engineers routinely perform security assessments of their own infrastructure, identify areas of weakness, and develop strategies to guard against potential attacks.
Job Titles
A cybersecurity engineering path translates into several specific job titles withcrucial roles in protecting sensitive data and systems. Some of the typical roles include:
- Security Engineer. These individuals design and implement secure network solutions to defend against advanced cyber threats and continuously monitor systems for breaches or anomalies.
- Application Security Engineer. They are focused on securing software applications against potential threats, which includes designing secure architectures and identifying and patching application vulnerabilities.
- Cloud Security Engineer. As businesses move more data and operations to the cloud, these professionals are critical in securing and protecting such cloud-based systems from breaches.
- Network Security Engineer. They are responsible for creating and maintaining secure networks within an organization, which includes installing and fortifying firewalls, configuring security devices, and identifying network vulnerabilities.
Prerequisites
Becoming a cybersecurity engineer requires a blend of formal education, industry certifications, and hands-on experience.
A bachelor’s degree in a field like computer science, information technology, or cybersecurity is a typical starting point, as these programs provide a foundational understanding of computing principles and programming languages.
Certifications also play a key role in this field, with credentials such as Certified Information Systems Security Professional (CISSP) or Certified Information Security Manager (CISM) often viewed as necessary qualifications.
Testing
Testing in cybersecurity refers to evaluating and scrutinizing various aspects of a system, application, or network to identify potential vulnerabilities that cyber threats could exploit.
Testers in cybersecurity apply methodical critical approaches to break down and analyze an organization’s cyber defenses. This can involve simulating cyberattacks, probing for weaknesses in software apps, analyzing network structures for potential weaknesses, and examining systems for coding errors or loopholes. The ultimate aim is to identify any weaknesses before cybercriminals do, thus preventing potential security breaches.
Job Titles
Testing is dynamic and expansive, involving a variety of specialized roles focusing on examining the different aspects of cyber defense mechanisms. Here are a few such roles:
- Penetration Tester. Often referred to as “ethical hackers,” penetration testers simulate cyberattacks on their own systems to identify vulnerabilities and assess the robustness of security measures.
- Vulnerability Assessor. These professionals specialize in discovering and analyzing vulnerabilities in systems and applications, helping to fortify cyber defenses preemptively.
- Security Auditor. Security auditors conduct comprehensive reviews of security systems to ensure they comply with industry standards and regulations and to identify any potential weaknesses.
Prerequisites
Testing often demands more specialized knowledge and cybersecurity skills than other paths. Though a formal degree isn’t always required to work in cybersecurity, acquiring relevant certifications like Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), or Certified Penetration Tester (CPT) can be highly beneficial if you want to work as a tester.
At the same time, hands-on experience via internships or similar roles isessential for building the key skills required to excel in testing.
Analysis
Cybersecurity analysis is the process of systematically examining data, systems, and patterns to understand and mitigate cyber threats. Cybersecurity analysts spend much of their time collecting and studying data related to their organization’s networks and systems, looking for patterns or anomalies that could signal a cyber threat. They also assess and evaluate security protocols, recommend improvements, and respond to security incidents.
In essence, analysts are the “detectives” of the cybersecurity world, drawing on a blend of technical skills and critical thinking to uncover and address potential threats before they can cause harm.
Job Titles
In cybersecurity, the risk analysis path offers a wide range of specialized roles, each focused on interpreting and using data to strengthen cyber defenses. Here are a few of these critical roles:
- Cybersecurity Analyst. They monitor and analyze an organization’s networks and systems, detect and respond to threats, and develop strategies to improve security protocols.
- Threat Intelligence Analyst. These professionals specialize in identifying and understanding emerging cyber threats, helping their organizations stay one step ahead of potential attacks.
- Security Operations Center (SOC) Analyst. Working in a SOC, these analysts monitor and analyze activity on networks, servers, endpoints, databases, and other systems to detect unusual behavior or security incidents.
- Intrusion Analyst. They focus on identifying attempted and successful cyber intrusions, understanding the tactics and techniques used by cyber attackers, and developing countermeasures.
Prerequisites
For roles in cybersecurity analysis, a foundation in computer science or a related field is often the first step,typically with a bachelor’s degree or an associates degree in some cases. If you don’t want to go the degree route, check out an alternative, such as Springboard’s Cybersecurity Bootcamp.
Beyond this, specific certifications can highlight an analyst’s ability to understand and respond to cyber threats. Certifications such as CompTIA Security+ are often sought by employers.
Response
Response in cybersecurity revolves around the strategies and actions taken when a cyber threat materializes into an actual security breach.
Professionals working in cybersecurity response are akin to digital first responders, springing into action when a breach occurs to minimize damage, eradicate the threat, and restore normal operations. Their tasks involve investigating the nature and extent of the breach, isolating affected systems, removing the threat, and implementing measures to prevent similar incidents.
Post-incident, they are also instrumental in analyzing the event to learn from the breach and improve the organization’s security posture.
Job Titles
Here are some examples of key roles within response in cybersecurity:
- Incident Responder. These professionals are the first line of defense when a cyber attack happens. They identify, respond to, and mitigate security incidents to limit damage and reduce recovery time.
- Cybersecurity Incident Manager. Incident managers coordinate the response during and after a cyber attack, ensuring effective collaboration among different teams and stakeholders.
- Forensic Analyst. These professionals investigate cyber-attacks to determine how the breach occurred, what information was compromised, and who was responsible, gathering evidence that can often be used in legal proceedings.
Prerequisites
Working on the response side of cybersecurity requires a solid foundational understanding of cybersecurity principles, strong problem-solving skills, and the ability to stay calm under pressure.
In addition to degrees and certifications, practical experience dealing with real-life security incidents is highly valuable. This maybe earned from roles in security operations centers (SOCs), digital forensics, or simulated incident response scenarios.
Auditing
Auditing in cybersecurity involves examining and evaluating an organization’s information systems, practices, and operations to ensure compliance with laws, regulations, and industry best practices.
Cybersecurity auditors scrutinize an organization’s cybersecurity policies, procedures, framework, and controls to detect and rectify any deficiencies or violations that could cause security breaches. Their goal is to ensure an organization’s compliance and advise on improving the overall security posture.
Job Titles
Here are a few key roles within this path:
- Cybersecurity Auditor. These professionals evaluate an organization’s cybersecurity strategies, policies, and systems, checking for compliance with regulations and identifying areas for improvement.
- IT Compliance Auditor. IT Compliance Auditors ensure that the organization’s technology and systems adhere to relevant laws, regulations, and internal policies, often with a strong focus on data privacy issues.
- Security Control Assessor. These assessors review and evaluate the effectiveness of security controls implemented in an organization’s IT systems.
Prerequisites
A career in cybersecurity auditing demands candidates with a blend of technical knowledge, an understanding of legal and compliance issues, and strong analytical skills.
While a computer science or cybersecurity degree can provide a solid foundation, a background in law or business may also be advantageous, given the role’s regulatory aspects.
Auditors often need several years of relevant work experience to understand the technical aspects of cybersecurity and how they intersect with business operations and regulatory environments.
Choosing a Path and Climbing the Career Ladder: Jobs at Different Levels
Choosing the right cybersecurity career path and moving up the ladder can seem complicated, but remember, every professional starts somewhere.
This section will guide you through different cybersecurity roles, from entry-level to senior positions, to help visualize your potential career progression and find the path that best suits your interests and skills.
Entry-Level Cybersecurity Jobs
Entry-level cybersecurity roles offer a perfect starting point for those just beginning their journey. They typically involve learning the ropes while being supervised and guided by more experienced team members.
- Cybersecurity Intern. As a cybersecurity intern, you’ll get hands-on experience with various tools and practices. You’ll likely work under the direct supervision of a cybersecurity professional, providing you with an excellent opportunity to learn, grow, and make valuable industry connections.
- Information Security Analyst. Information security analysts monitor an organization’s network and investigate when security breachesoccur. They’re the eyes and ears on the ground, swiftly identifying and addressing any suspicious activities.
- IT Auditor. An IT auditor’s role is to evaluate an organization’s information systems, ensuring they comply with applicable laws and standards. Even in this entry-level position, your work will impact the integrity of your organization’s data and infrastructure.
Mid-Level Cybersecurity Jobs
Mid-level roles require more experience and skills. They offer an opportunity to handle more responsibilities, engage in strategic decisions, and often specialize in a particular area of cybersecurity.
- Penetration Tester. As a penetration tester, you’ll think like a hacker but act like a guardian. Your job is to find and exploit vulnerabilities in your organization’s systems before real attackers do, ensuring that these systems are as secure as possible.
- Security Engineer. Security engineers are the builders and protectors of the cybersecurity world. In this role, you’ll design and implement secure network solutions to protect against advanced cyber threats. You’re not just maintaining defenses. You’re actively constructing them too.
- Forensic Analyst. As a forensic analyst, you’ll become a digital detective. When a cyber incident occurs, you’ll examine the “crime scene,” tracing the footsteps of cyber attackers, identifying how they broke in, and collecting evidence to help prevent future attacks.
Senior Cybersecurity Jobs
Senior-level roles are leadership positions that require a high level of expertise. These roles often involve overseeing cybersecurity strategy, making critical decisions, and leading teams.
- Cybersecurity Architect. As a cybersecurity architect, you’ll be in charge of the big picture. You’ll design complex and comprehensive security systems that protect an organization’s digital infrastructure. Your decisions will play a significant role in safeguarding your organization’s cyber environment.
- Chief Information Security Officer (CISO). Climbing to the chief information security officer role, you’ll be the top authority on all things cybersecurity in your organization. CISOs develop and implement the organization’s security strategy, manage a team of security professionals, and are the main point of contact for all security-related issues.
What Do Cybersecurity Salaries Look Like?
Here’s what you can expect to make at various stages of your cybersecurity career:
Entry-Level
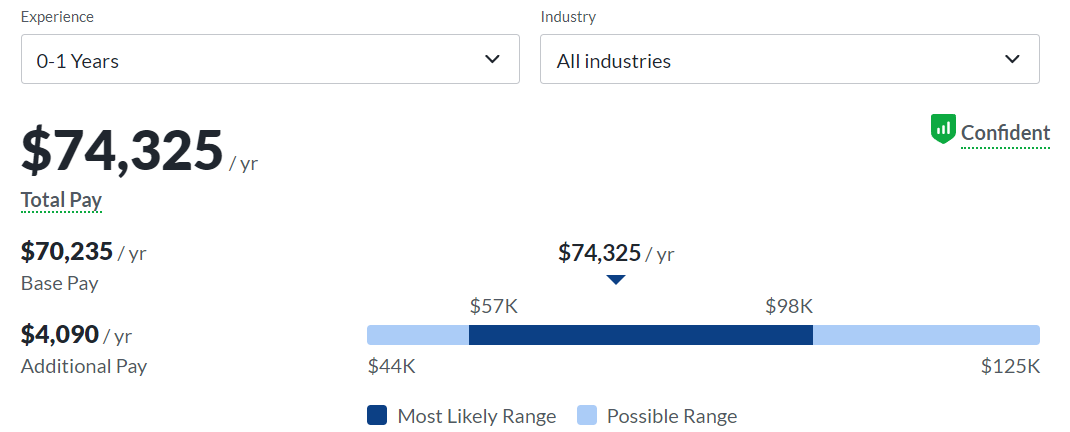
Entry-level cybersecurity professionals can expect to earn an average starting pay of $74,325 per year.
Mid-Level
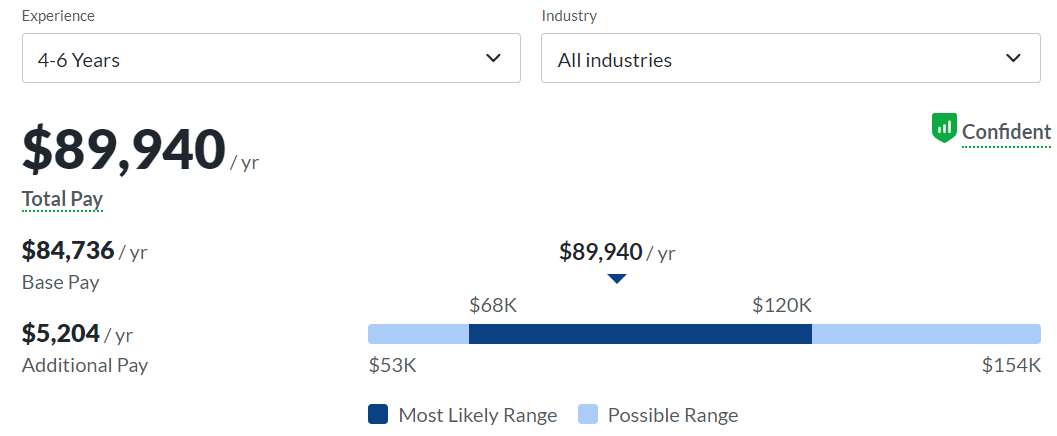
Mid-level cybersecurity professionals with 4-6 years of experience earn an average annual salary of $89,940.
Senior
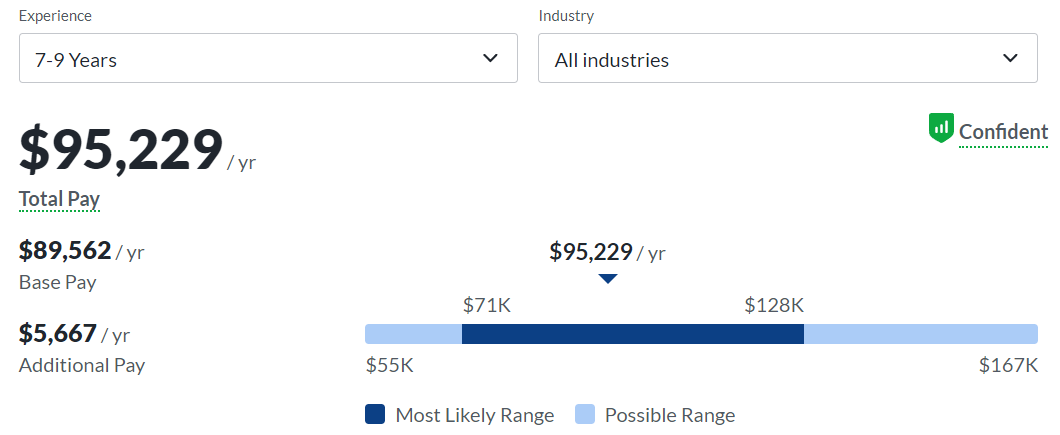
Senior-level cybersecurity professionals with at least seven years of experience earn an average of $95,229 per year, while those with more than ten years of experience earn an average of $105,124.
How To Start a Career in Cybersecurity: General Requirements
Embarking on a cybersecurity career requires careful planning and preparation. Understanding the necessary skills, qualifications, and experiences that will help you navigate and succeed in this field is essential.
Here’s what you need to know about starting a career in cybersecurity.
Foundational Knowledge
Foundational knowledge of computer systems, networks, and coding is essential for any cybersecurity role.
This fundamental understanding forms the basis of your cybersecurity career, allowing you to grasp how systems are exploited and how to build defenses against these exploits. This knowledge equips you with the technical vocabulary of cybersecurity and is a crucial factor employers consider when hiring.
Education and Learning
While a degree in computer science or a related field can provide an in-depth understanding of key concepts, enrolling in online courses or bootcamps can also be a great way to learn about cybersecurity.
In this ever-evolving field, continuous learning is a must. New threats and security measures are constantly being developed, and staying up to date is crucial for your career progression.
Skills and Tools
Cybersecurity professionals require a mix of technical and soft skills.
Technical skills can range from knowledge of encryption algorithms to understanding network protocols, while soft skills include problem-solving, critical thinking, and effective communication.
Familiarity with tools like firewalls, intrusion detection systems, and security information and event management (SIEM) software is also essential.
Certifications
Certifications are highly valued in cybersecurity, as they demonstrate to employers that you have the required expertise and dedication to your professional growth. They can significantly increase your job prospects and salary potential by validating your skills and keeping you updated with the latest trends and practices in the field.
Experience
Previous experience is highly valued by employers. If you’re just starting out, you can gain practical experience through internships, volunteering, or personal projects. These opportunities allow you to apply theoretical knowledge, gain hands-on skills, and demonstrate your commitment to the field.
Real-life experience will also help you better understand your interests and skills, enabling you to choose a path that suits you best in cybersecurity.
Other Prerequisites
Strong ethical standards are crucial in cybersecurity due to the sensitive nature of the work. A passion for learning and staying updated with the latest threats and defenses is also necessary.
Finally, a willingness to take on challenges and a persistent attitude can go a long way in this field, as solving complex security problems can often require significant effort and creativity.
Get To Know Other Cybersecurity Students
Catherine McKoy
Consumer Compliance Systems Analyst at Alaska USA Credit Union
Rafael Ayala
Mergers And Acquisitions at Autodesk
Eric Rivera
IAM Security Specialist at Dearborn Group
Landing a Cybersecurity Role and Climbing the Career Ladder: Real-Life Examples and Paths To Learn From
There’s tremendous value in observing and learning from other people who navigated the cybersecurity space successfully. Let’s look at two real-life examples and paths to learn from.
Chigozie Asikaburu
Chigozie’s journey is full of insights for anyone standing at the crossroads of a cybersecurity career. Initially majoring in computer science, he stumbled into cybersecurity through a research program.
What’s noteworthy about this example is how he weighted various factors before diving headfirst into the field. His story demonstrates the importance of evaluating personal preferences and market dynamics when carving out a career path that’s both lucrative and fulfilling.
Sandra
Our second example is a video by Sandra outlining the different career paths one can take as a cybersecurity professional. She discusses several key considerations, such as picking the right certifications, switching jobs or keeping the same one for longer, diving into management roles, or working independently.
Sandra emphasizes that there’s no one-size-fits-all career path in cybersecurity and encourages viewers to consider their own skills, interests, and career goals when making these decisions.
FAQs About Cybersecurity Career Paths
We’ve got the answers to your most frequently asked questions.
Is Cybersecurity a Good Career?
Cybersecurity is an excellent career choice for many reasons. It’s a rapidly growing field with high demand for skilled professionals due to increasing cybersecurity threats. It also offers competitive salaries, opportunities for continuous learning, and the chance to make a significant impact by protecting critical information and systems.
How Do I Plan for a Career in Cybersecurity?
Planning for a career in cybersecurity involves understanding your interests and skills, researching different career paths in the field, and determining the required qualifications and experience. It’s also crucial to stay updated on the latest cybersecurity trends, threats, and technologies.
What Skills Do You Need for a Career in Cybersecurity?
Cybersecurity requires a mix of technical and soft skills. Technical skills include knowledge of networks, programming languages, and an understanding of a wide variety of security systems and threats. Soft skills include problem-solving, critical thinking, and effective communication.
What Degree Is Best for a Career in Cybersecurity?
Degrees in computer science, information technology, or cybersecurity can all lead to a career in cybersecurity. However, the field is interdisciplinary, so degrees in mathematics or physics can also be valuable, especially when combined with relevant cybersecurity certifications and practical experience.
How Do I Get Started in Cybersecurity Without Any Experience?
Starting a cybersecurity career without any experience can be challenging, but it isn’t impossible. Begin by self-studying through online courses, books, and free resources. Volunteering, joining cybersecurity competitions, or working on personal projects can also provide practical experience and make your resume more attractive to potential employers.
Since you’re here…
Interested in a career in cybersecurity? With or Cybersecurity Bootcamp, you’ll get a job in the industry, or we’ll return your tuition money. Test your skills with our free cybersecurity course, and check out our student reviews. We’re a safe bet. 🔒😉