Free Cybersecurity Course
Enter the cybersecurity field with our free introductory course. Learn the basics and build a strong foundation.
With more than three-quarters (77 percent) of Americans online daily and a growing number of internet-connected devices in and around the house, it comes as no surprise that cyberattacks on cities, corporations, and individuals remain a serious problem. This spring, the city of Atlanta endured a crippling ransomware attack, arguably one of the most impactful cyber breaches against a large American city (it took five days for the city government’s computers and printers to get back up and running).
The Identity Theft Resource Center’s 2017 Annual Data Breach Year-End Review revealed that 11 percent of cyber breaches on businesses came from unauthorized access (e.g., cracking passwords). One-fifth of breaches involved credit and debit cards, up 6 percent from 2016. And a staggering 830 breaches included social security numbers. This drives home the fact that no city, country, business, or individual is 100 percent safe from malicious outsiders (or insiders—90 percent of companies admitted feeling more vulnerable to insider attacks). But taking proactive steps does mitigate risk.
Cryptography to the Rescue

(Image source: Wikimedia Commons)
One such cyber asset is cryptography, a technique to secure data and communications. This powerful tool has won wars (consider the Navajo code talkers, who used encrypted code to relay sensitive information) and is talked about more than you may realize (a “SpongeBob Squarepants” episode contains a prime example of cryptography in action).
The end goal? Protect personal information and make it safer for users to send messages over public spaces without unwanted cyber threat. But how exactly does cryptography accomplish this? Is cryptography just another name for encryption? And what are some ways users can bulletproof their email messages using encryption, leaving intrusive eavesdroppers frustrated and defeated?
Cryptography Basics: Encryption vs. Cryptography, Cipher vs. Encryption
Cryptography is the study of secure (yet accessible) communications. Encryption and ciphers fall under this umbrella. Encryption is the process of turning text into code. A cipher is that actual code. Think of encryption as the driving force of cryptography. But how does basic encryption work?
Basic Encryption: The Sword Cryptography Wields
Let’s say you need to send your boss company-sensitive information. Without the proper encryption methods (i.e., digital signature, etc.), you are more likely to suffer from a successful man-in-the-middle attack, where the silent but dangerous intruder can eavesdrop and even impersonate a sender or receiver. Thanks to encryption software, your message turns from plaintext (e.g., “Hi Sandra, attached is the…”) to ciphertext (e.g. “percent6 (0$5, @94*47df kp &th…”), making it harder for outside parties to crack.
The Nuts and Bolts of Cryptography: How the Process Works

(Image source: Unsplash)
But let’s get into the nitty-gritty details. Putting a magnifying glass up to the hypothetical email message you just sent your boss, here’s how it got to your boss’ inbox in one piece.
You type up your message and send it to the encryption program along with your encryption key (remember, we need both encryption and decryption programs for this to work). As mentioned, the normal, readable message (or plaintext) you created transforms via encryption to a jumble of unreadable characters (ciphertext) and is sent over the internet to your boss.
Now on your boss’ end: She receives the ciphertext, which hopefully is left untampered (no man-in-the-middle attack). In a perfect world, the ciphertext transforms via her decryption program and decrypting key back into your original plaintext message, and the cryptography process is complete.
Get To Know Other Cybersecurity Students
Karen Peterson
Compliance Advisory Associate at Coalfire
Eric Rivera
IAM Security Specialist at Dearborn Group
Rafael Ayala
Mergers And Acquisitions at Autodesk
Fighting Cyber Crime Using a Basic Encryption Algorithm
There are two main ways the cryptography process works: asymmetric-key encryption and symmetric-key encryption. Put simply, symmetric-key encryption is when the encryption and decryption key matches; asymmetric-key encryption is when they don’t. But, as with cryptography, there’s more to it.
What Is Symmetric-Key Encryption?
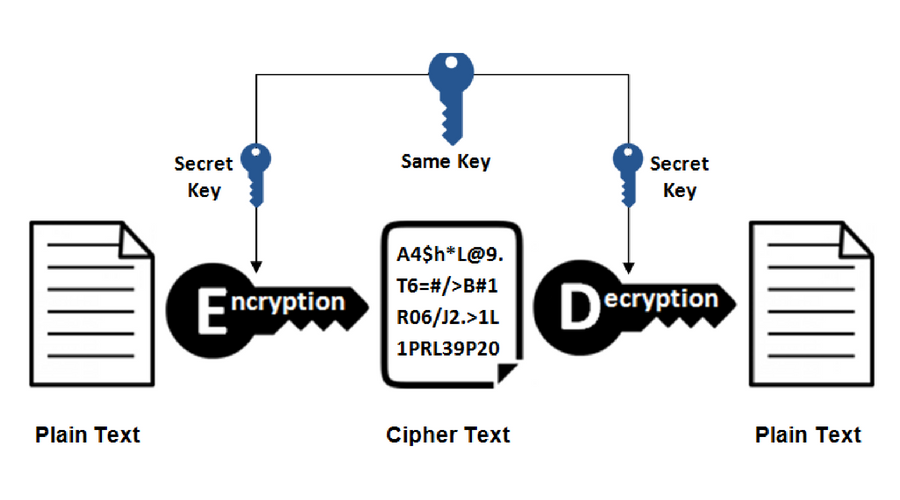
(Image source: SSL2BUY)
Symmetric-key encryption, or private-key encryption, encrypts and decrypts using one shared (yet private) key. Its algorithm, or cipher, is typically speedy and efficient. Plus, it’s great for storing encrypted documents. Encrypted communications, however? Not so much. The key must be kept secret at all times by both the sender and the receiver; if one leaks, the encryption method is a bust. You’d then think that private-key encryption was an outdated encryption algorithm, but it’s actually not, and here’s why.
Related: Understanding PKI Basics
Myth Buster: Private-Key Encryption Is Not a Weak Defense
A little over two decades ago, the National Institute of Standards and Technology (NIST) decided to use a private-key cipher as the encryption standard for U.S. government agencies. Long story short, inventors created a 128-bit private-key cipher that became the Advanced Encryption Standard (AES). How secure is the code? It would take billions of years for a supercomputer running a brute force attack to crack it.
What Is Asymmetric-Key Encryption?
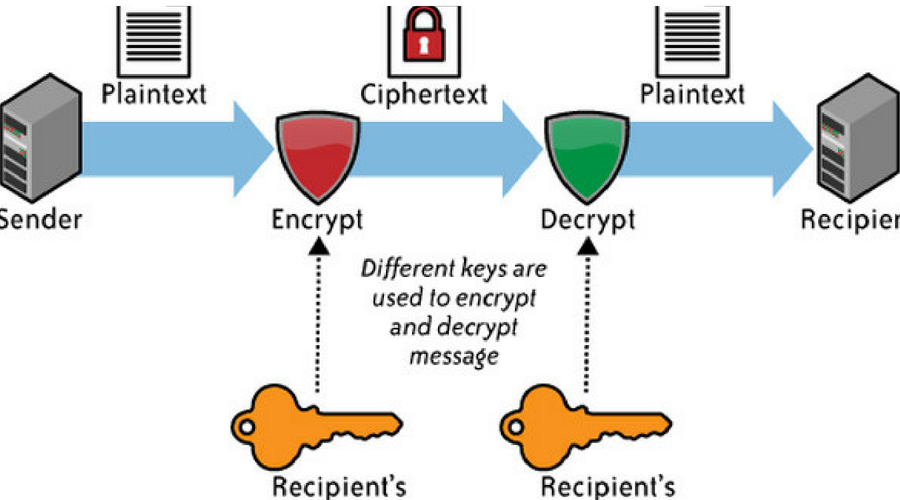
(Image source: The ICT Lounge)
When it comes to email encryption, asymmetric-key encryption (or public-key encryption) is your go-to. The reason? Unlike symmetric-key encryption, asymmetric-key encryption uses not one but two keys—one private, one public. Anyone can access the public key; technically, the sender uses the receiver’s public key when sending a message. However, only the receiver can use their private key to decrypt it. The same goes in reverse.
How to Keep Your Personal Information Safe
While there will always be cyber threats—especially in the age of IoT—thankfully more internet traffic is encrypted than not. What you’ll see is more web pages with the green lock HTTPS symbol to the left of the URL (especially since, as of 2015, Google favors HTTPS over non-HTTPS sites), signaling that the site is more secure than its older HTTP cousin.
The good news doesn’t stop there; according to a Grand View Research report, the encryption software market is expected to hit $8.4 billion by 2024, which translates to a compound annual growth of more than 14 percent from 2016 to 2024. Still, there’s more progress to be made: 65 percent of internet users cite memorization as the top way to keep track of passwords, and less than one-tenth of Gmail users rely on two-factor authentication. It’s poor cyber-hygiene practices like these that make it easy for spammers, spoofers, and hackers to walk through the virtual front door. But you can protect yourself with these encryption tips:
- Play it safe and always use two-factor authentication
- Use password-management software to stay on top of passwords
- Only visit HTTPS-secure sites
- If you run a website, make sure it is HTTPS-secure for cybersecurity (and search engine) purposes
- When emailing, stick with public-key encryption
- Completely install encryption methods on company databases
- Create a digital signature on your emails, so family, friends, and colleagues know you are you
Take advantage of these encryption tips to ward off spammers, spoofers, and hackers. Being cyber-ready now reduces stress and the chances of a successful cyberattack.
Related Read: What Does a Cybersecurity Analyst Do?
Since you’re here…
Breaking into cybersecurity doesn’t take a Trojan Horse. Our Cybersecurity Bootcamp lasts just six months, and we’re ready to help you land a job after graduation or your money back. There’s urgent need in this field, so we’re beaming out tons of freebies to entice you, like this email course on certifications and our guide to becoming a software security analyst. Join in—there are plenty of jobs to go around!